Do you own a Plantronics headset? If you do, you are probably using Plantronics Hub on your system. This software can be used to configure the headset and complete firmware upgrades.
As I went through the documentation of Plantronics Hub I noticed something interesting:
“PLTHub.exe is the Plantronics Hub process that runs at start up
providing all of the functionality expected from Plantronics Hub.
PlantronicsUpdate.exe is also a process that runs at start up. This
process allows Windows users without administrative permissions
to upgrade Plantronics Hub.”
Which means that there is a privileged process that can be triggered from a non-administrator context. My curiosity was raised!
What I did next was to install the application in a version, which was not the latest one on a test system and launch Process Monitor. Filters were applied to only list actions from the elevated and the user process. After that I choose to upgrade the application through the user GUI. The output of Procmon is shown below:
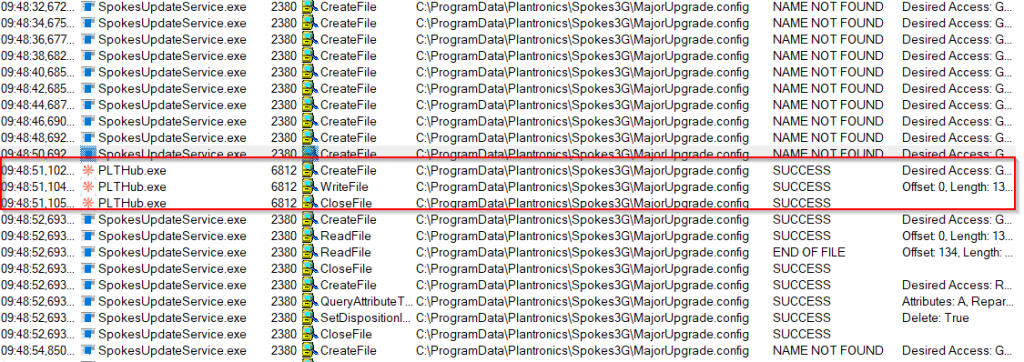
As can be identified from the output the elevated process “SpokesUpdateService.exe” is continuously probing for a file called “MajorUpgrade.config” in “C:\ProgramData\Plantronics\Spokes3G\”. The user application “PLTHub.exe” creates this file, which means that any user is able to create the corresponding file. The elevated process immediately consumes the file and deletes it. The update process was finished shortly after. I reverted back to the old version and retriggered the update process, but this time I stopped the service “SpokesUpdateService.exe”.
Now I was able to view the contents of the “MajorUpgrade.config” file and the contents were:
markus|advertise|C:\Users\Markus\AppData\Local\Temp\PlantronicsHub\sec0pdbgi8tl92mykzw1jnao3h6rv5fu4qx7\PlantronicsHubBootstrapper.exe
So basically, the file consists of the following structure <username>|advertise|<path to exe>
I went ahead and modified the path to the executable file with the following path “C:\Windows\System32\cmd.exe”, restarted the update service and was immediately given an elevated command prompt.
The issue was reported to Poly and they handled it professionally. Their fix was to make sure that the update executable is signed with their certificate. I tried to bypass their new validation (for example with a downgrade attack) but failed.
Affected Version: Plantronics Hub for Windows prior to version 3.14
CVSS v3: 7.3 (AV:L/AC:L/PR:L/UI:R/S:U/C:H/I:H/A:H)
CVE-2019-15742: https://support.polycom.com/content/dam/polycom-support/global/documentation/plantronics-hub-local-privilege-escalation-vulnerability.pdf
Exploit-DB: https://www.exploit-db.com/exploits/47845
Exploit was ported to Metasploit by bcoles: https://github.com/rapid7/metasploit-framework/blob/master/modules/exploits/windows/local/plantronics_hub_spokesupdateservice_privesc.rb